The computers weren’t on the Net or a LAN. The very last thing you ought to do is make sure your computer’s HOST file is repaired, as it’s normally damaged by svchost.exe. You merely must open the application, press the browse button, choose the corrupted file that is to be mended, and choose the correct option. Moreover, there are many data recovery software that can be found for download on the web. The new program includes the capability to find all your financial details about the principal page, and you may have invoices paid as scheduled with your Quicken program. While there are a lot of software programs readily available, only few are totally free.
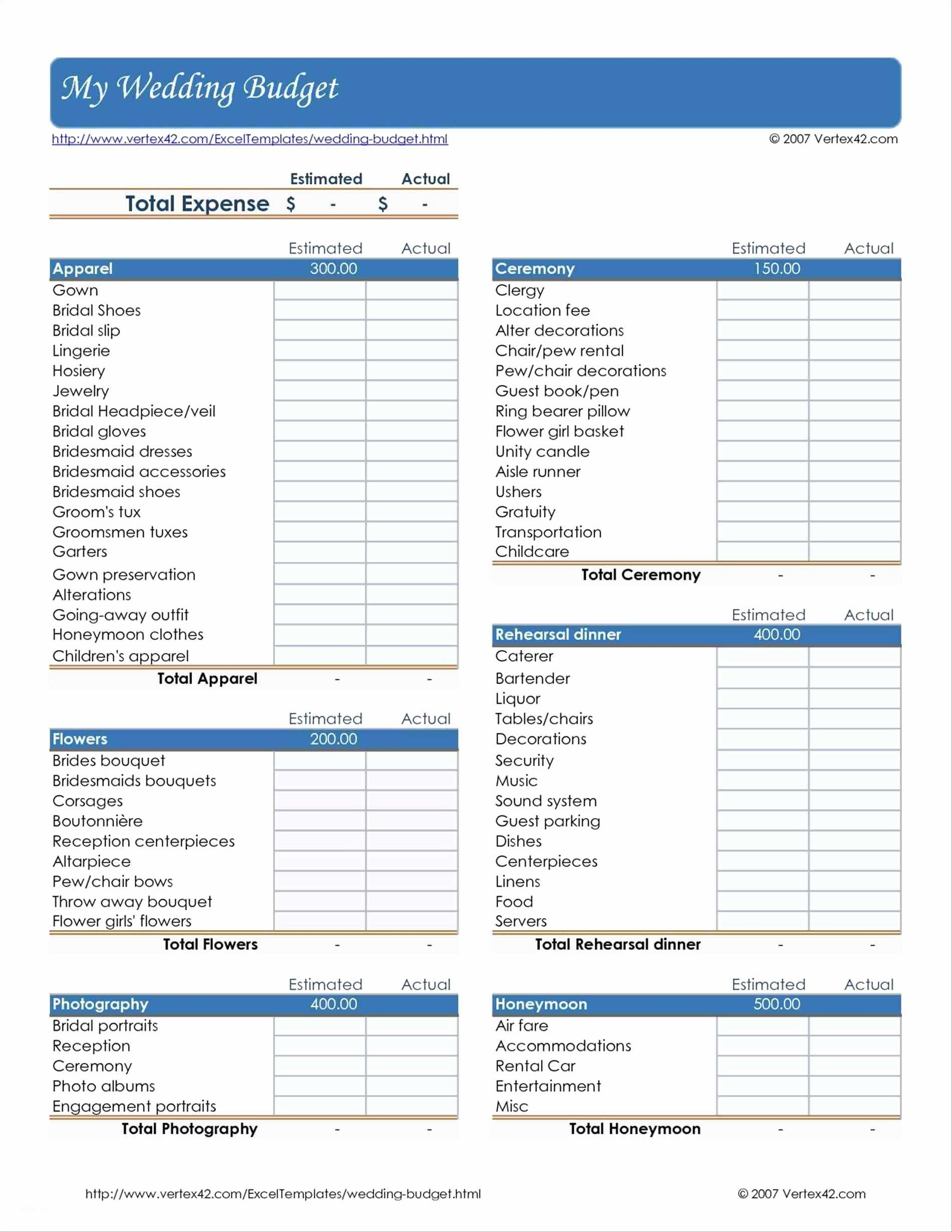
Wedding Budget Spreadsheet Printable Throughout Indian Wedding Budget Spreadsheet As Well As Line Wedding Bud Uploaded by Adam A. Kline on Wednesday, January 23rd, 2019 in category Download.
See also Wedding Budget Spreadsheet Printable With Printable Wedding Budget Spreadsheet For Mac Bud Luxury 50 Fresh from Download Topic.
Here we have another image Wedding Budget Spreadsheet Printable Throughout Destination Wedding Budget Spreadsheet Elegant Wedding Bud Worksheet featured under Wedding Budget Spreadsheet Printable Throughout Indian Wedding Budget Spreadsheet As Well As Line Wedding Bud. We hope you enjoyed it and if you want to download the pictures in high quality, simply right click the image and choose "Save As". Thanks for reading Wedding Budget Spreadsheet Printable Throughout Indian Wedding Budget Spreadsheet As Well As Line Wedding Bud.