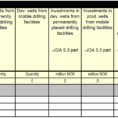
The PCI DSS (Payment Card Industry Data Security Standard) contains a very simple set of guidelines for processing payments on the Internet. It is important that companies who process credit card payments take the recommendations of the standards as they will protect the security of your customers and you. The…
Tag: pci dss 3.2 requirements spreadsheet
Pci Dss 3.2 Requirements Spreadsheet
The PCI DSS 3.2 requirements are to be the benchmark of business security. Therefore, it is very important for you to have a reference to guide you through the standards and regulations when it comes to these policies. In addition, the guidelines in this document have been formulated by third…