In the event the document might not be opened, then you want to insert it into a new document to recoup its content. Another process to recoup corrupted files is to connect the document into a brand-new complete file. When it’s to do with saving files that are important, it’s always advised to maintain a backup in a data storage device. Click the excel file which you have to open. If there are a number of people organizing the credential files, we suggest using the on-line choice to stop duplication of efforts. After clicking on the folder icon, then a list of folders which you have will look and you’re going to select where to set your file. Then click on’Open’, and decide on the WPS file you want to see.
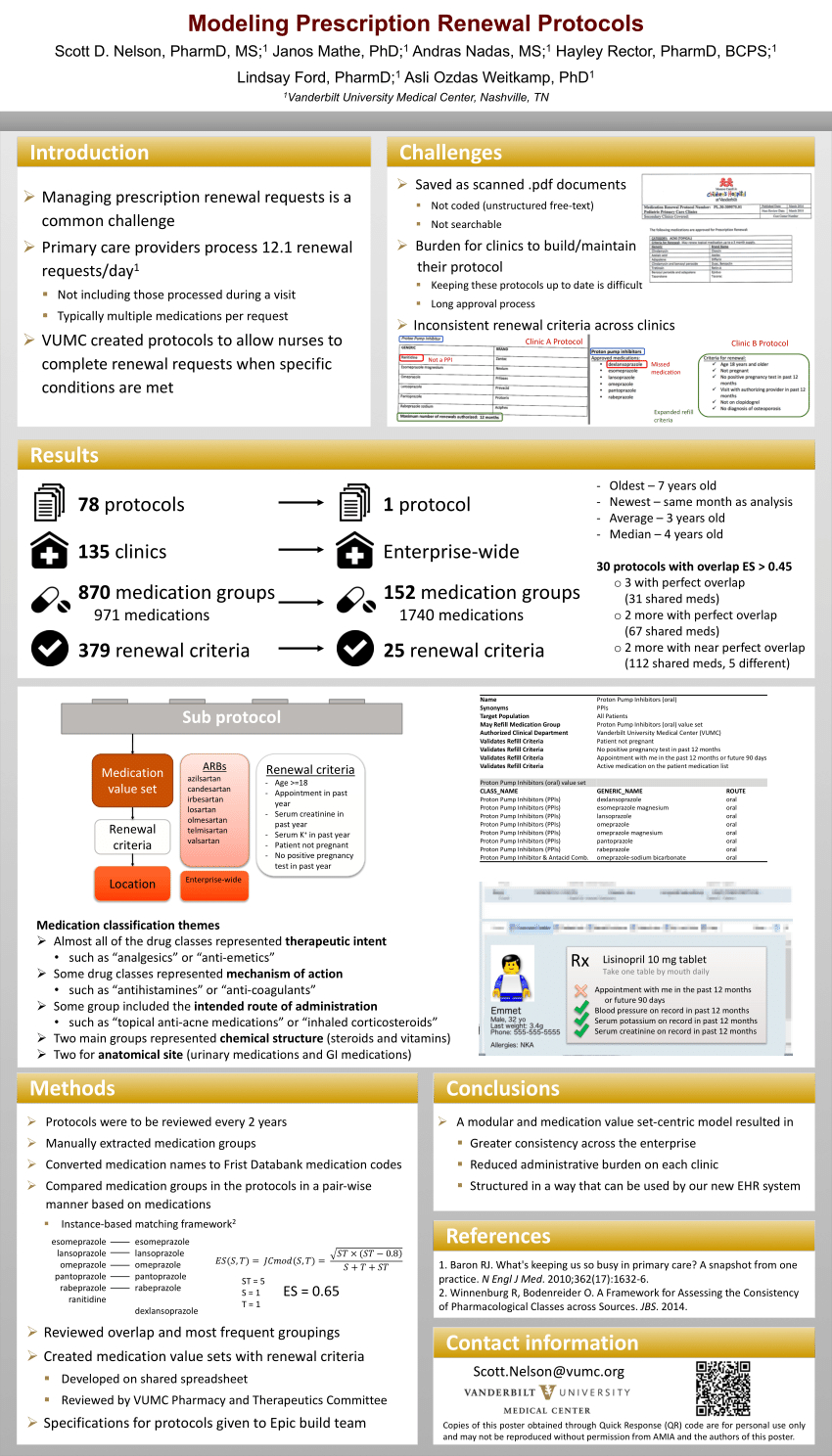
Prescription Refill Spreadsheet For Pdf Modeling Prescription Refill Protocols Uploaded by Adam A. Kline on Wednesday, January 23rd, 2019 in category 16, Download.
See also Prescription Refill Spreadsheet Throughout Pdf Modeling Prescription Refill Protocols from 16, Download Topic.
Here we have another image Prescription Refill Spreadsheet With Regard To Prescription Sheet Template Medication Log Templates Free Pinterest featured under Prescription Refill Spreadsheet For Pdf Modeling Prescription Refill Protocols. We hope you enjoyed it and if you want to download the pictures in high quality, simply right click the image and choose "Save As". Thanks for reading Prescription Refill Spreadsheet For Pdf Modeling Prescription Refill Protocols.