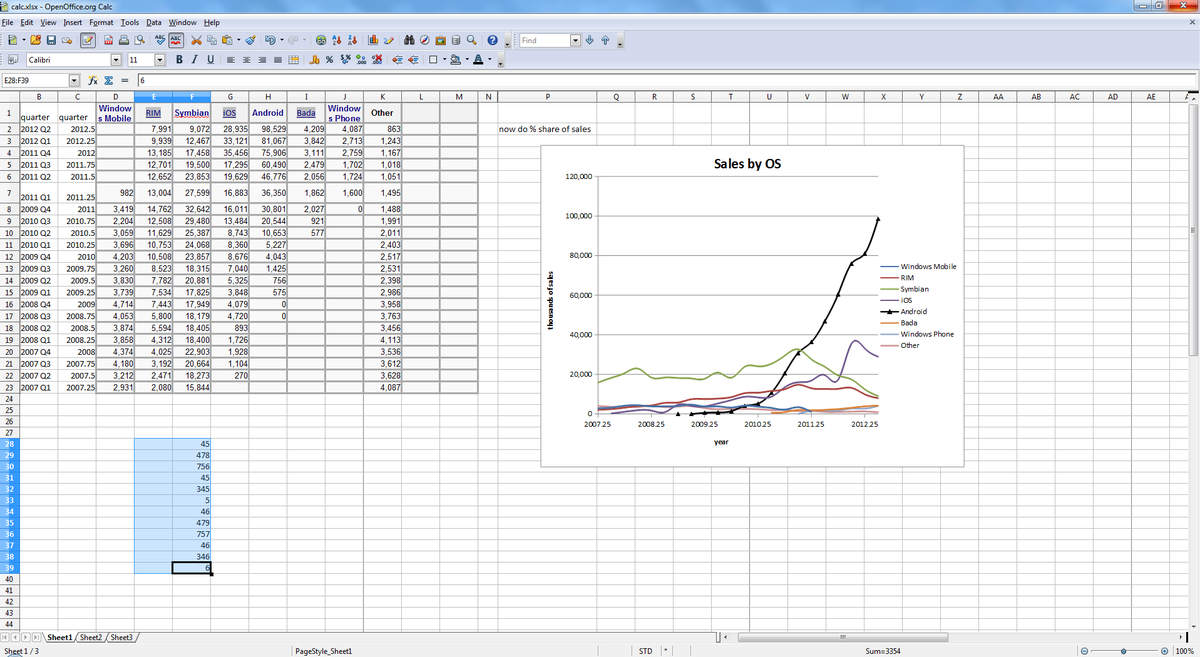
Lotus 1 2 3 Spreadsheet Free Download | Papillon Northwan With Lotus Spreadsheet Download Uploaded by Adam A. Kline on Friday, November 2nd, 2018 in category 1 Update, Software.
See also Lotus 123 Software Free Download For Windows 8 | Papillon Northwan With Lotus Spreadsheet Download from 1 Update, Software Topic.
Here we have another image Taking A Look At Ibm Lotus Symphony Spreadsheets – Page 5 – Techrepublic With Lotus Spreadsheet Download featured under Lotus 1 2 3 Spreadsheet Free Download | Papillon Northwan With Lotus Spreadsheet Download. We hope you enjoyed it and if you want to download the pictures in high quality, simply right click the image and choose "Save As". Thanks for reading Lotus 1 2 3 Spreadsheet Free Download | Papillon Northwan With Lotus Spreadsheet Download.