The Foolproof Ffiec Cybersecurity Assessment Tool Excel Spreadsheet Strategy
Label software is inexpensive in the event that you would love to explore that option. This tool was made to be utilized in lieu of cumbersome checklists by giving a top down approach to the identification of high risk areas to permit for appropriate tailoring of audit programs which will bring about audit efficiencies. Please note that it is. Our completely new security controls mapping tool can be found at SecurityCheckbox.com. The tool may also be used after changes are implemented to measure their effects on risk and preparedness throughout the organization. Fortunately, you can accomplish this by employing the selection tool. For this reason, you should work with business users and management to make a list of all valuable assets.
If you are searching for Cyber Security Template Scoring Worksheet you’ve come to the perfect spot. Spreadsheets can even be used to make tournament brackets. They are generally utilised to take care of data. They can keep an eye on your favourite player stats or stats on the full team. An excel spreadsheet, this checklist includes all the proper questions that has to be asked during an SSAE-16 review, with a simple risk ranking metric that will permit you to compare all important vendors.
The spreadsheet is situated on the FDIC site. Our betting pool spreadsheet is extremely simple to use. At times developing a recorder calls for an excellent deal of time, thus the templates that are offered in word format can help stack your data in an efficient method. They are an excellent time saving feature that can allow you to save you a fantastic deal of energy and time. Spreadsheet templates are used by a massive spectrum of individuals owing to its period effectiveness. It’s possible to likewise see absolutely free spreadsheet template.
Ffiec Cybersecurity Assessment Tool Excel Spreadsheet Secrets
The pain-points for various organizations will be different. The DSP is really the most extensive document we’ve made and it’s targeted for enterprise-class organizations with a need to align to the subsequent frameworks. NIST recommends organizations utilize the builder periodically so that they can maintain the maximum level of cybersecurity readiness. The WISP is approximately 2% of the price for a consultant or 5% of the price of your internal staff to create equivalent documentation. The OCC and FFIEC answers are made to foster additional industry and examiner comprehension of the Assessment. While the FFIEC’s CAT is an adequate place to begin, it is hard to use, it’s not collaborative, it doesn’t track your changes with time, and as we’ve observed in the software business, if it’s not simple to use then people will merely utilize it begrudgingly if REQUIRED to achieve that. Often, auditors employ testing that test” controls which are merely procedural based and aren’t relevant in they don’t have an immediate connection to preventing or detecting errors.
A number of the requirements are particular to the handling of CUI, while some are put on the whole network, all users or the entire facility. In this manner, it’s very easy to find out what the requirements for cybersecurity are and where to learn how to implement them. Accordingly, you have to define a standard for specifying the value of each asset. This alternative is designed to permit an institution the ability to fulfill the prerequisites of the declarative statement indirectly with other security measures controls and a degree of flexibility not previously allowed. One choice is to utilize Microsoft’s STRIDE method, which is easy, clear and covers the majority of the top threats.
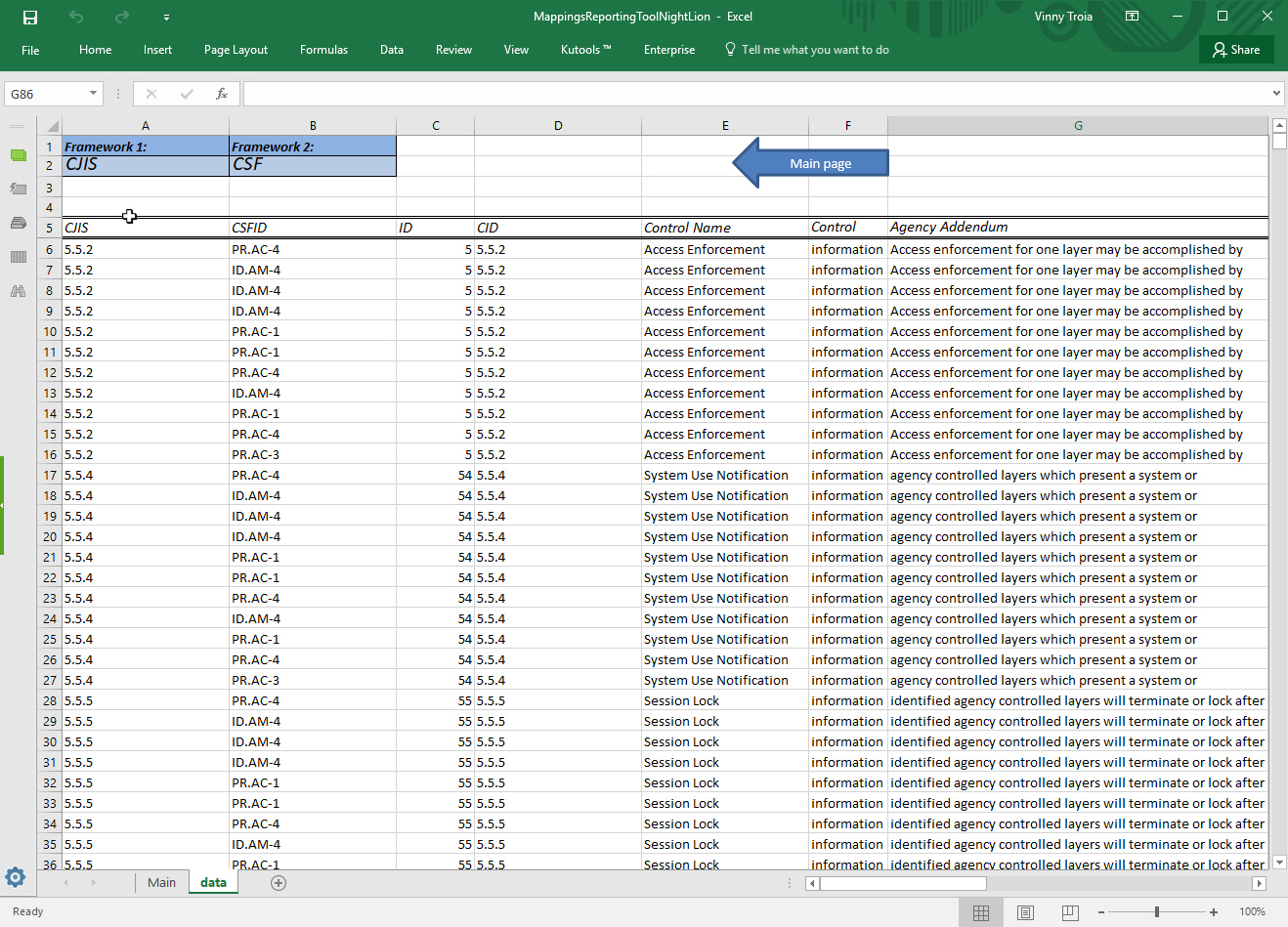
Third, we have to spot vulnerabilities. The Cybersecurity Maturity part of the tool was made to help us measure a credit union’s degree of risk and corresponding controls. Therefore, the IFCR component is the dominant issue.
It’s possible to map up to five frameworks. As the tool’s implementation evolves over the duration of the calendar year, we’ll be certain to continue to keep stakeholders informed. If management determines that the institutions maturity levels aren’t appropriate in connection with the inherent risk profile, management should think about reducing inherent risk or creating a strategy to enhance the maturity levels. The Assessment is intended to offer a measurable and repeatable procedure to assess an institution’s degree of cybersecurity risk and preparedness. Our reports provide risks ranked by means of a risk tolerance score that’s fully customized to your organization, along with remediation strategies necessary to get ready for audit.
The Fundamentals of Ffiec Cybersecurity Assessment Tool Excel Spreadsheet Revealed
Control maturity is assessed dependent on implementation of certain discrete elements. By way of example, suppose you need to estimate the risk related to the threat of hackers compromising a specific system. This threat is always high, regardless of what business you’re in. The probability of system failure rides on the caliber of your computer For relatively new, high-quality equipment, the opportunity of system failure is low. All these factors will impact the difficulty related to effective implementation. This activity will probably take a complete day for smaller organizations and lots of days for bigger ones. Specifically, better communication can be accomplished by having a wholesome mixture of experts on each side of the aisle who understand the SOX framework, the significance of SOX compliance and ultimately, the ability to come up with efficiencies in testing and reporting.
Sample for Ffiec Cybersecurity Assessment Tool Excel Spreadsheet