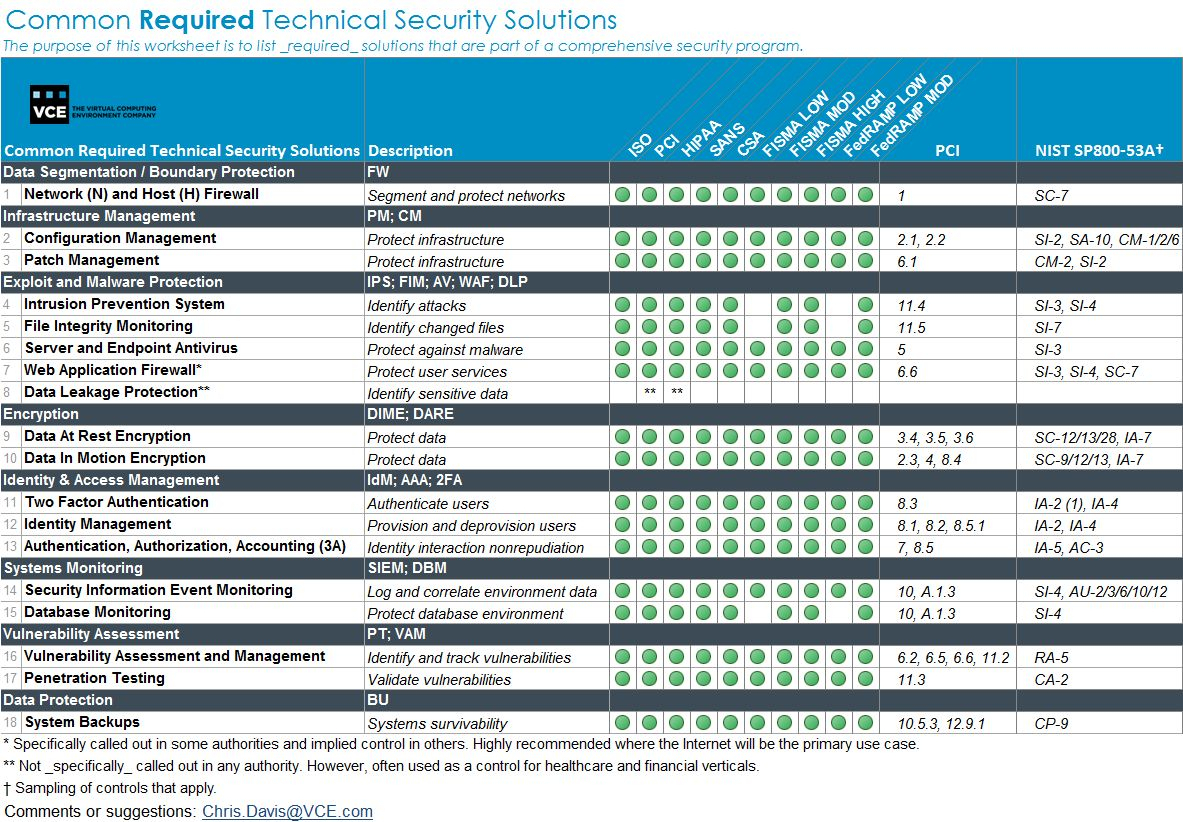
Fips 199 Spreadsheet Features
Electronic documentation (for example, intranet pages) are just like paper documents, in fact better in the feeling they are simpler to control and update. Choose the format that you want to convert the document to. Once downloaded, you ought to be in a position to open the Works document.
Be certain your DR plan addresses the entire recovery procedure, from backup to restore to cleanup. Basically, that application invokes its DR program. It’s very likely additionally to select custom-made applications that may be used with your little small business practice. Bookkeeping applications is often as simple as a homemade dictionary but with additional facets which might have significant financial advantages of the organization. In the same way, don’t await a disaster to occur before checking your users can access the DR atmosphere. They need to understand how to undertake the actions in GCP that they’re used to accomplishing in the production environment, like logging in, accessing VMs, and so on. This server is currently ready for configuration.
Your network might have an outage, your most recent application push might introduce a crucial bug, or maybe you someday have to contend with a pure disaster. By way of example, in the instance of historical compliance-oriented data, you most likely don’t require speedy access to the data, thus a large RTO value and cold DR pattern is acceptable. Make certain that you grant users the very same accessibility to the DR environment they have in the source manufacturing atmosphere.
Details of Fips 199 Spreadsheet
The non-free manner is to utilize Works Document Viewer for Mac. Moreover, the demo will restore a few strings of information from every form it analyzes so that you may realize that the data is intact and usable. You may see the available bundles here. Please check the modifier employed for that specific procedure code, it could be invalid or inappropriate or missing. Occasionally more than 1 FIPS code has to be utilized to create a desired data collection. A census tract FIPS code comprises six digits. If you would like to procure more details, click the logo below.
A codicil is a distinct document, signed later, that changes a number of the conditions of the will. The SoA may, for example, take the shape of a matrix identifying various forms of information risks on a single axis and risk treatment options on the other, showing the way the risks must be treated within the body, and perhaps who’s accountable for them. SoA denotes the output from the info risk assessments and, particularly, the decisions around treating those risks. A full BCP isn’t workable and requires proactive solutions to ease the chance of downtime. Developing a BCP for customers is no simple undertaking. All CONUS per diem prices are determined dependent on county. June 28, 2019 Users of this site should be mindful I don’t do much with the web site.
Create a test atmosphere. 1 common question we receive from clients pertains to aligning with the proper security framework to guarantee they have the suitable coverage for compliance. The regular means to do it is to have a look at your RTO and RPO values and which DR pattern you’re able to adopt to fulfill those values. It’s also reasonable to say that business drivers might be vague term. See the data dictionary for additional information. Choose the Works document.
Things You Should Know About Fips 199 Spreadsheet
In healthcare, for example, an organization should comply with HIPAA guidelines. By way of example, organizations that are looking to do charge card transactions will need to obey the Payment Card Industry (PCI) data security standard. That’s why companies must do a little bit of degree of threat modeling to work out which vulnerabilities are most risky to their enterprise. To develop a suitable plan, a business must determine the probability of danger. A little business is not as likely to have a hot site available. A massive enterprise experiencing downtime is more uncommon in today’s age.
Incorporate users that are logging into the DR environment as a portion of the normal DR tests that you implement. If you’re using an alternate identity system, make sure accounts are synced with your Cloud Identity account. The exact same controls you have in your production environment must be relevant to your recovered atmosphere.
The most difficult part of establishing a mature SOA-based enterprise framework of reusable small business services is a powerful governance model. Additionally, GCP’s focus on administrative simplicity usually means that the expenses of managing an intricate application are reduced too. Part of your DR planning is to make certain that the software you rely on is prepared for a recovery event. The plan consists of details that assist in mitigating risk in front of a disaster. Plan where you would like to host your CD environment and artifactsthey must be available and operational in case of a disaster. It’s unlikely a 1 size fits all plan will apply to each customer. When you design your DR program, you should combine your application and data recovery tactics and examine the larger picture.