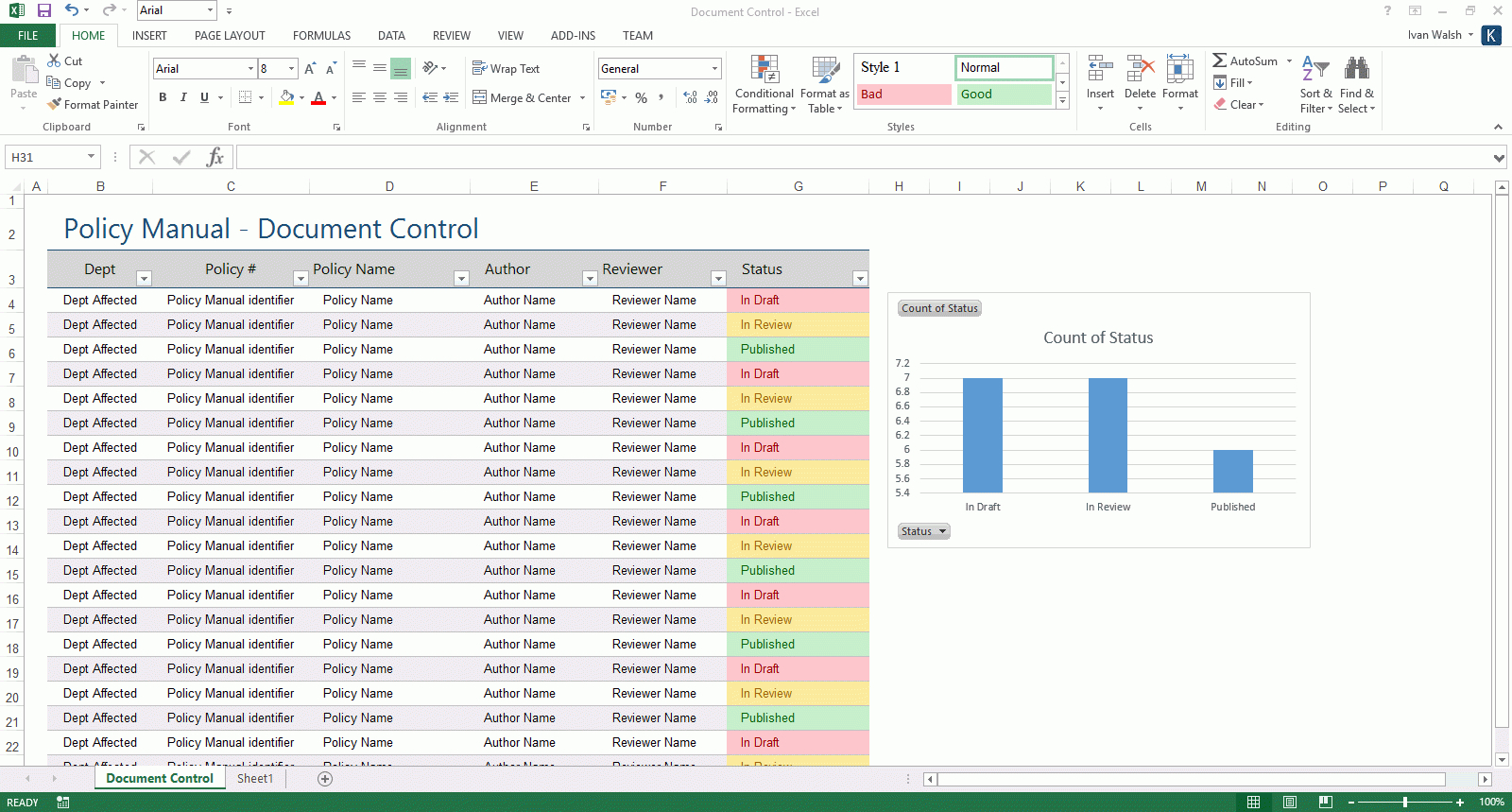
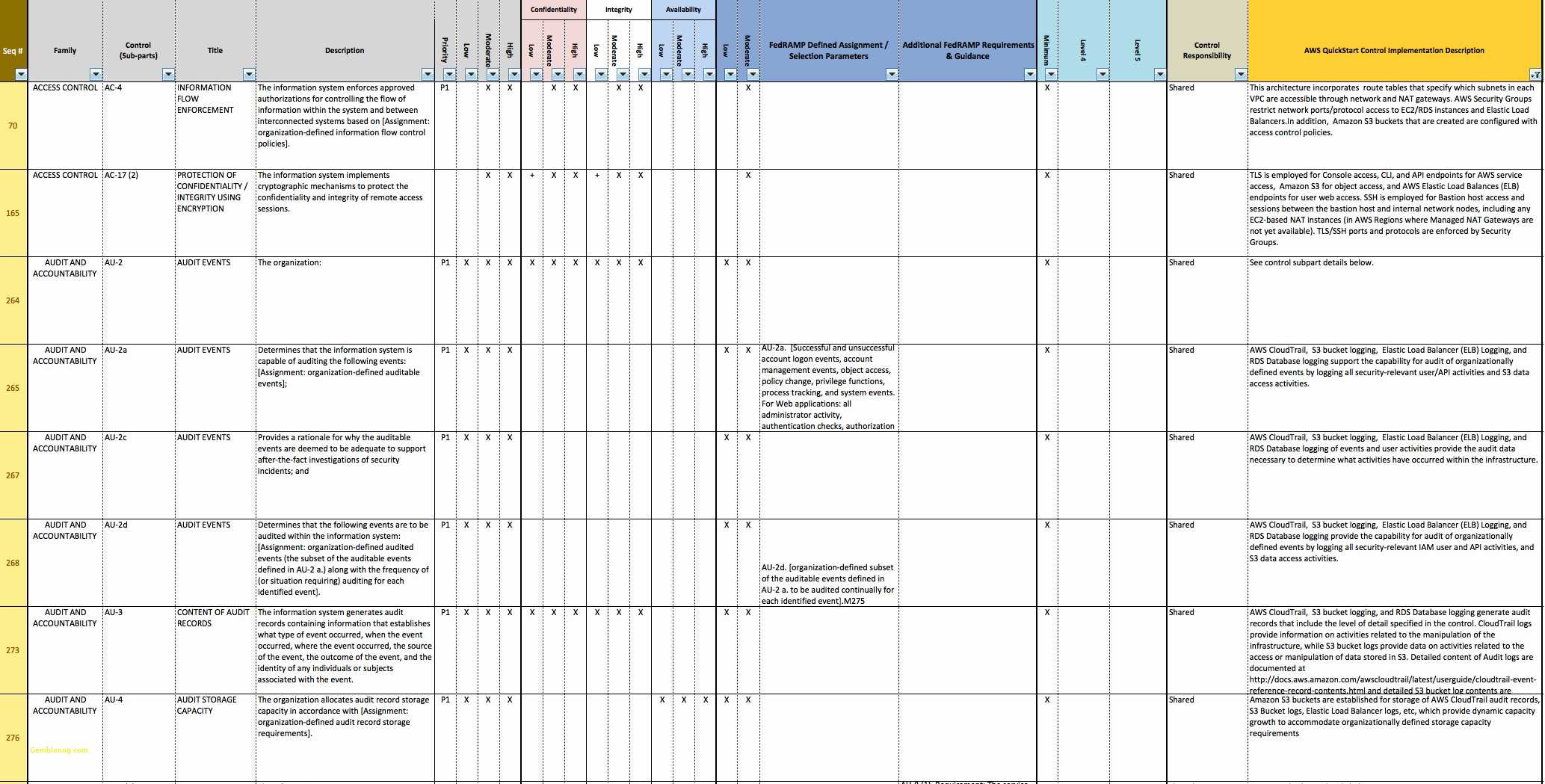
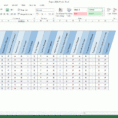
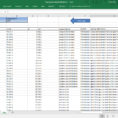
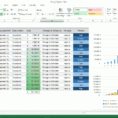
A Security Controls spreadsheet is used to define the components that are part of a high-level security control. Security controls consist of software or hardware devices and/or applications that are placed in and around a building or site to minimize access to it by unauthorized users.
Critical security controls are typically defined on a series of sheets which are called Security Controls Sheets. These sheets are used as a guide for the implementation of the various hardware, software, and processes that are required for high level security control. The sheets will include:
The following are some of the most common critical security controls:
How to Define Security Controls Using a Security Controls Spreadsheet
Perimeter Controls – Perimeter controls are to prevent people from entering or exiting a restricted area of a building or site. By contrast, they are the least intrusive of the types of security controls. A perimeter control is normally an application that makes use of video surveillance to monitor the area around a restricted area of a building or site. This application can be a device or software that monitors the area around the perimeter of a building or site and sends alerts or notifications to the control system if any unauthorized person is detected.
Security Device Controls – These types of controls are used to create a strict set of rules and regulations for a location to be used for a certain purpose, such as housing or a museum. This control is generally a handheld device that is monitored by a control panel.
Data Center Security – These are used to protect a data center against unauthorized access to data. By contrast, the data-center security controls is more sophisticated than the perimeter controls. data-center security controls includes methods such as a password, encryption, logs, and policies.
Key Management Controls – Some of the more popular key management controls include the use of the keypad, touch pad, or voice recognition, amongst others. These controls provide higher level security by using a keypad to identify the owner of a code.
Highly Sensitive Security Systems – These types of security systems are used to classify individuals or areas of a building that are highly classified. The systems are usually not very intrusive, but they may be able to monitor other areas in the building and only allow access to those areas that are highly sensitive.
Access Control Database – This type of database is used to make use of a detailed data set, which includes the specific purpose and information about a user. This type of database can be used for many things, but typically it is used to keep track of all information related to certain personnel.
Real Time Network Monitoring – Real time network monitoring is used to help detect rogue behavior and intrusion by unauthorized users. This type of monitoring is done by a control panel, which can monitor all networks on a specific network.
If you would like to have a view into the different kinds of security controls available, then you should take a look at the Security Controls spreadsheet. It is an easy to understand visual based system that is perfect for creating a high-level security control sheet to help you define the components of a security system. PLEASE READ : 1099 expense spreadsheet
Sample for 20 Critical Security Controls Spreadsheet